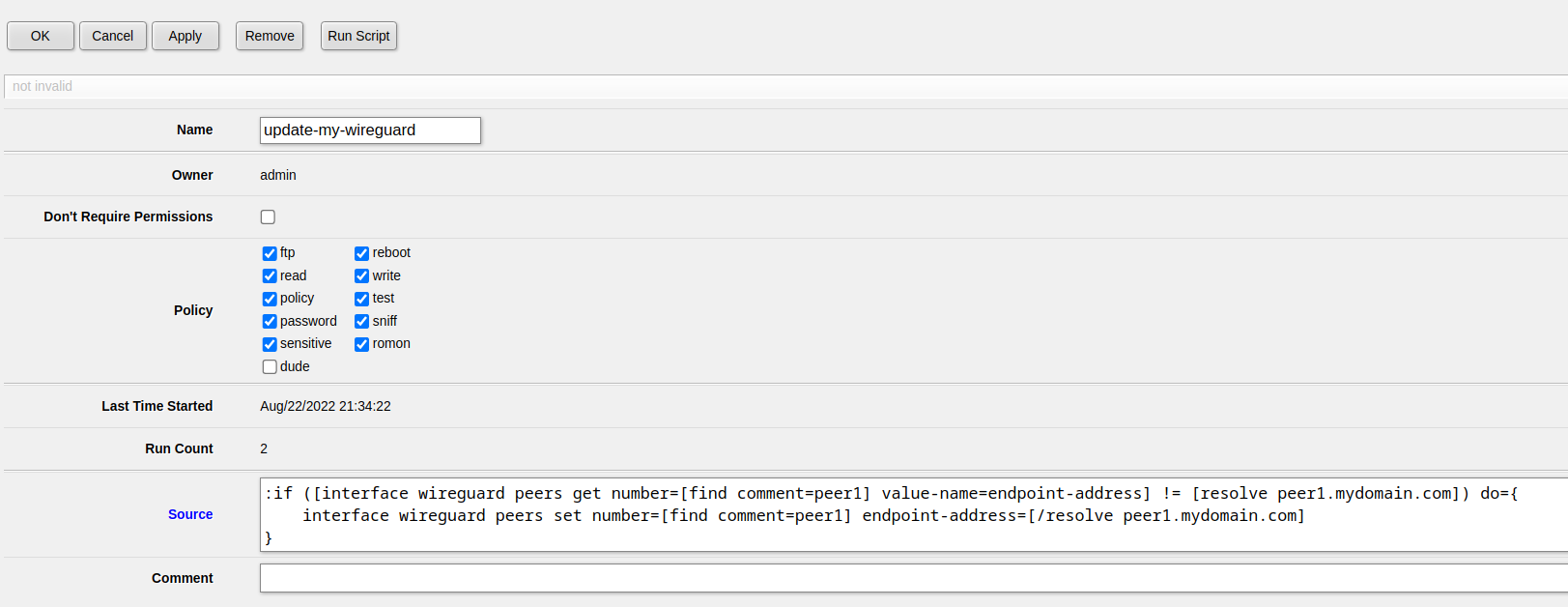
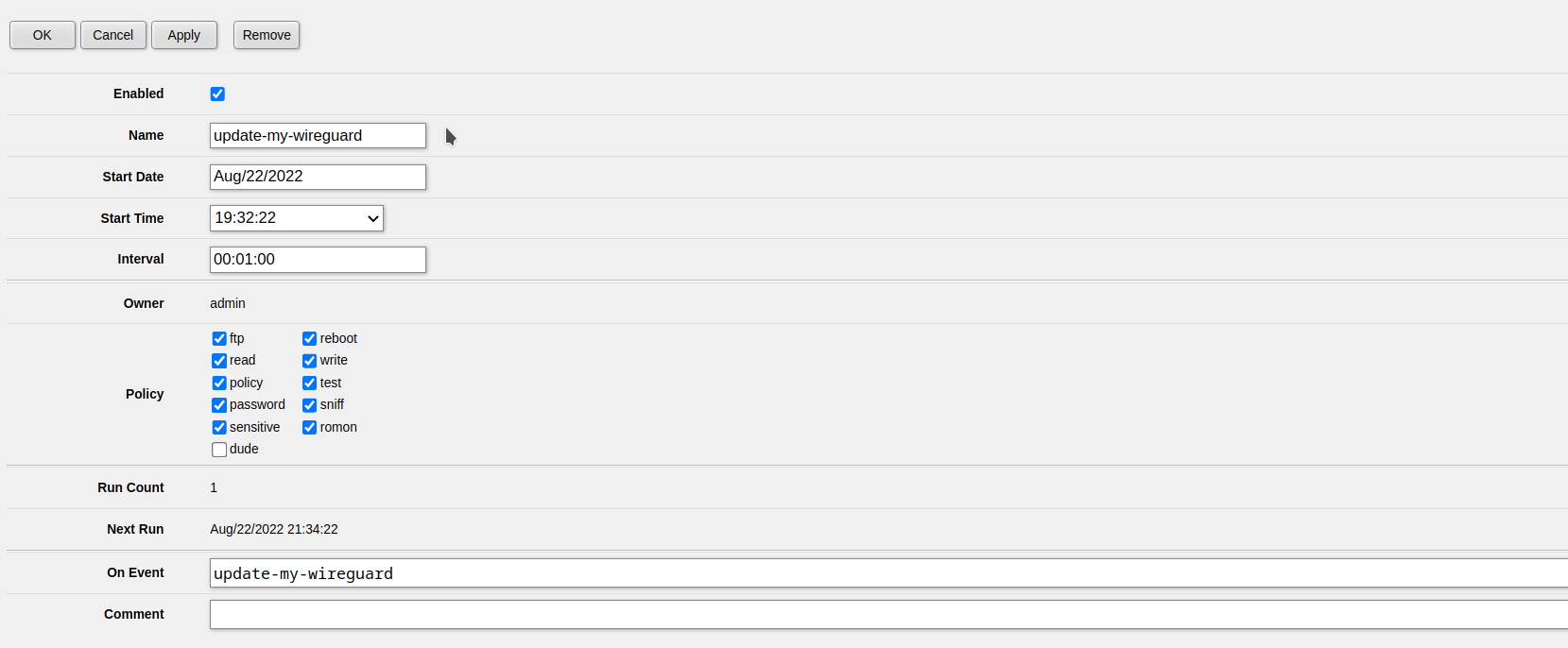
In this example we will use Wireguard-ESP32-Arduino in order to make HTTP requests over Wireguard on the ESP32.
[env:esp32-gateway]
platform = espressif32
board = esp32-gateway
framework = arduino
monitor_speed = 115200
lib_deps =
ciniml/WireGuard-ESP32@^0.1.5#include <WiFi.h>
#include <WireGuard-ESP32.h>
// WiFi configuration --- UPDATE this configuration for your WiFi AP
char ssid[] = "MyWifiESSID";
char password[] = "my-wifi-password";
// WireGuard configuration --- UPDATE this configuration from JSON
char private_key[] = "gH2YqDa+St6x5eFhomVQDwtV1F0YMQd3HtOElPkZgVY=";
IPAddress local_ip(10, 217, 59, 2);
char public_key[] = "X6NJW+IznvItD3B5TseUasRPjPzF0PkM5+GaLIjdBG4=";
char endpoint_address[] = "192.168.178.133"; // IP of Wireguard endpoint to connect to.
int endpoint_port = 19628;
static WireGuard wg;
void setup()
{
Serial.begin(115200);
Serial.println("Connecting to the AP...");
WiFi.begin(ssid, password);
while( !WiFi.isConnected() ) {
delay(100);
}
Serial.println(WiFi.localIP());
Serial.println("Adjusting system time...");
configTime(9 * 60 * 60, 0, "ntp.jst.mfeed.ad.jp", "ntp.nict.jp", "time.google.com");
Serial.println("Connected. Initializing WireGuard...");
wg.begin(
local_ip,
private_key,
endpoint_address,
public_key,
endpoint_port);
}
void loop()
{
WiFiClient client;
/**
* Connect to
* python3 -m http.server
*/
if( !client.connect("10.217.59.1", 8000) ) {
Serial.println("Failed to connect...");
delay(1000);
return;
} else { // Client connected successfully. Send dummy HTTP request.
client.write("GET /wireguard-test HTTP/1.1\r\n");
client.write("Host: wireguard.test.com\r\n");
client.write("\r\n\r\n");
}
}Remember to replace 192.168.238.133 by the IP address of the computer your ESP32 should connect to (i.e. the computer running WireGuard). You also need to enter the correct Wifi credentials.
On the computer, deploy this WireGuard config:
[Interface]
# Name = Computer
PrivateKey = ONj6Iefel47uMKtWRCSMLan2UC5eW3Fj9Gsy9bqcyEc=
Address = 10.217.59.1/24
ListenPort = 19628
[Peer]
# Name = ESP32
PublicKey = H3KaL/X94984cLDNWFsM4Hx6Rs/Ku0bW2ECkDUn7wFw=
AllowedIPs = 10.217.59.2/32
PersistentKeepalive = 60
which is auto-generated by the following GuardMyWire config:
{
"rules": {
"Node": {
"connect_to": ["*"],
"keepalive": 60
}
},
"peers": [
{
"name": "Computer",
"endpoint": "192.168.178.233:19628",
"addresses": [
"10.217.59.1/24"
],
"type": "Node",
"interface_name": "wg0"
}, {
"name": "ESP32",
"addresses": [
"10.217.59.2/24"
],
"type": "Node",
"interface_name": "wg0"
}
]
}
Enable this config and start a Python HTTP server to receive the requests using
python3 -m http.server
Now flash the firmware on the ESP32.
Using wg show you should see the ESP connecting:
interface: Computer
public key: X6NJW+IznvItD3B5TseUasRPjPzF0PkM5+GaLIjdBG4=
private key: (hidden)
listening port: 19628
peer: H3KaL/X94984cLDNWFsM4Hx6Rs/Ku0bW2ECkDUn7wFw=
endpoint: 10.9.1.108:19628
allowed ips: 10.217.59.2/32
latest handshake: 5 seconds ago
transfer: 11.71 MiB received, 10.43 MiB sent
persistent keepalive: every 1 minute
Look for the
latest handshake: 5 seconds ago
line.
On the shell running python3 -m http.server you should see the dummy HTTP requests:
10.217.59.2 - - [31/Dec/2021 02:36:48] "GET /wireguard-test HTTP/1.1" 404 -
10.217.59.2 - - [31/Dec/2021 02:36:48] code 404, message File not found
10.217.59.2 - - [31/Dec/2021 02:36:48] "GET /wireguard-test HTTP/1.1" 404 -
10.217.59.2 - - [31/Dec/2021 02:36:48] code 404, message File not found
10.217.59.2 - - [31/Dec/2021 02:36:48] "GET /wireguard-test HTTP/1.1" 404 -
10.217.59.2 - - [31/Dec/2021 02:36:48] code 404, message File not found