Problem:
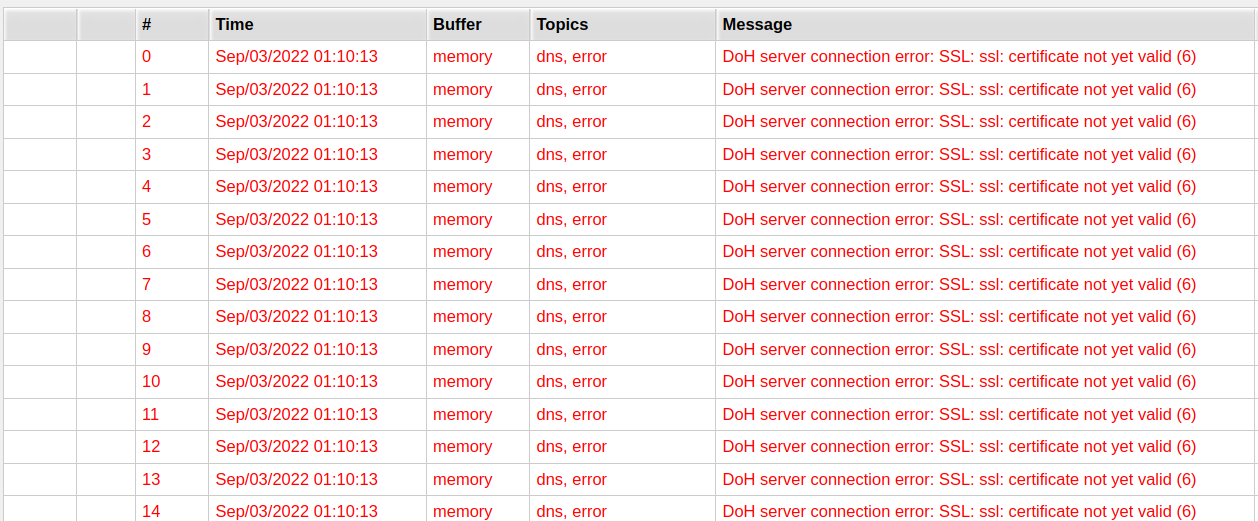
The DNS server integrated into your MikroTik router doesn’t work and the log shows a lot of
DoH server connection error: SSL: ssl: certificate not yet valid (6)
messages:
Reason for the error:
The issue here is that the clock in your MikroTik router does not (yet) know the correct time.
For example, the clock might be set to 1st of January, 1970 – however, the TLS certificate of the DNS-over-HTTPS server is only valid from, for example, 1st of November, 2022. This is why the MikroTik router tells you that the certificate isn’t valid.
Preferred solution: Fix the time using NTP
Just tell the MikroTik server to get the time from a public NTP server.
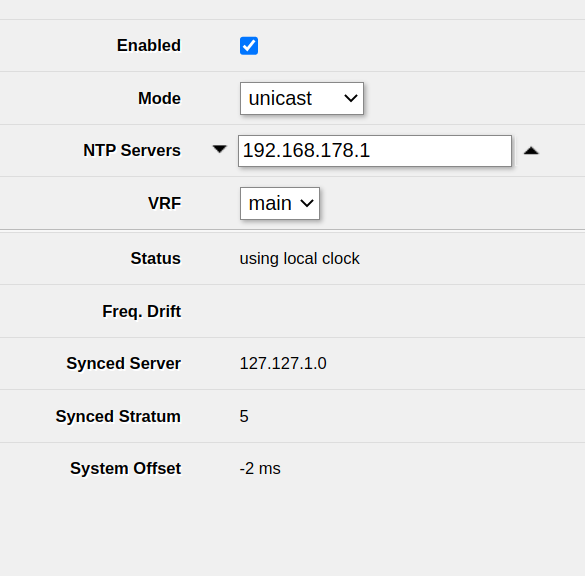
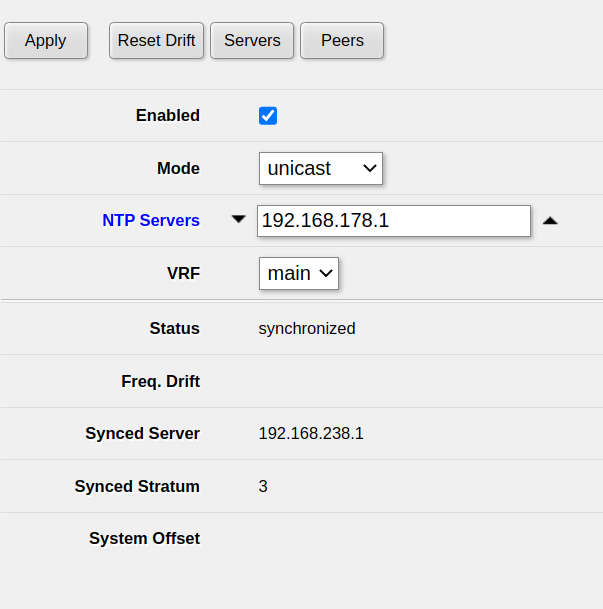
Open System -> NTP client in WebFig or Winbox. Typically, you want to use the upstream router as an NTP server. In my case, that is 192.168.178.1.
Ensure that Enabled is checked, add the NTP server and click Apply.
After waiting a few seconds, you should see synchronized under Status. This means that the clock of the MikroTik router has been set correctly and the issue should be fixed.
Alternate solution: Disable DNS-over-HTTPs
This solution decreases the security of your system and is hence not preferred. You should always set the time of your router correctly, not doing so will lead to a bunch of issues.
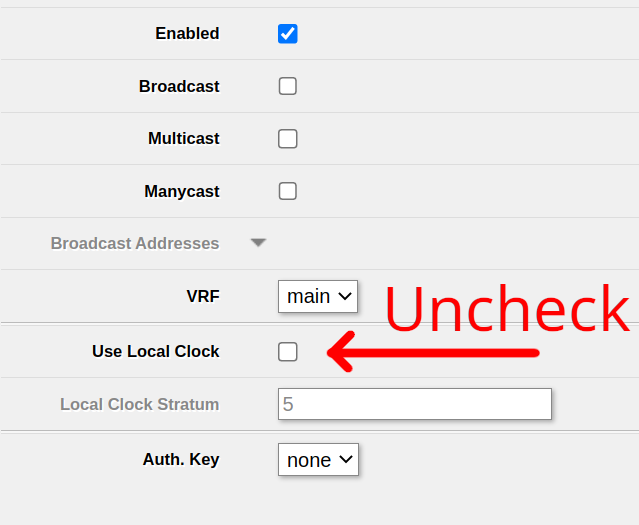
If you, however, still intend to disable DNS-over-HTTPS, open IP -> DNS and remove all servers under Use DoH servers, then click Apply.
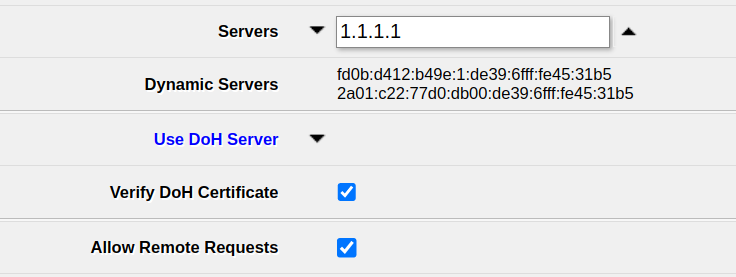
After that, your router will use the normal DNS servers – 1.1.1.1 in my case. Ensure to enter some server there to make sure DNS requests work – if in doubt, you can always use 1.1.1.1 (Cloudflare) or 8.8.8.8 (Google).
Note that requests to those servers will neither be encrypted nor authenticated, so requests can be sniffed and/or manipulated by anyone capable of manipulating traffic to your device. Even though DNS-over-HTTPS is slighly slower (which, in turn is alleviated by the caching feature of the MikroTik router’s DNS server), it provides a huge security benefit.
 then click
then click